- Dictionary > Purdue model
What is the Purdue model?
The Purdue model is a part of the Purdue Enterprise Reference Architecture (PERA) developed to model and visualize flows for network-connected OT systems. This model was first introduced in 1992 by Theodore J. Williams of the Purdue University Consortium.
The model advocates for classification into 5 layers/zones, with modern implementations adapting the model by adding a layer as a security buffer between OT and IT, commonly referred to as DMZ and/or layer 3.5.
This customized model can be visualized most simply as shown below.
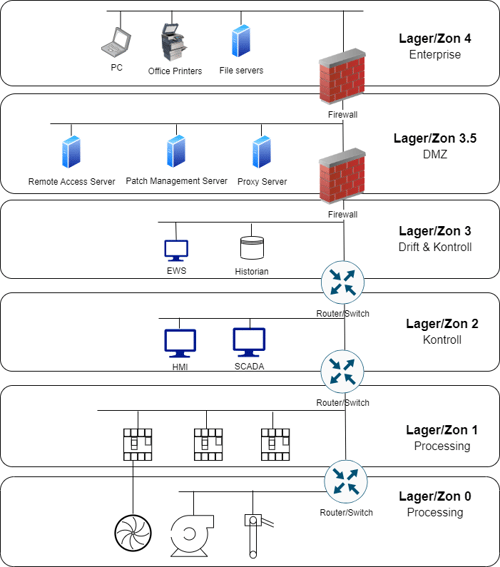
Figure A: Simplified visualization of the customized Purdue model.
Purdue Layer/Zone 0
Zone 0 consists of sensors, actuators, motors, and other components used to physically control and/or measure processes. These are often combined to create complete chains for automated manufacturing with conveyor belts and robots. Communication typically occurs using customized protocols, either directly connected to PLC/RTU or through network connections.
Purdue Layer/Zone 1
Zone 1 holds the intelligence that controls the devices in Layer 0, with these devices typically falling into one of the following categories:
- Programmable logic controllers (PLC) utilize input data to execute device control. The input data can be either measurements from devices in Layer 0 or input from systems in Layer 2.
- Remote terminal units (RTU) primarily act as a link between devices in Layer 0 and Layer 2, lacking their control logic.
Purdue Layer/Zone 2
Zone 2 houses more traditional IT equipment tailored for process control, historically custom-built from the ground up for specific purposes. The primary systems categories include:
- Supervisor Control and Data Acquisition (SCADA) systems that monitor and manage physical processes, whether locally or remotely connected. These systems often aggregate data sent to historical storage.
- Human-Machine Interface (HMI) is primarily used for easy control and monitoring, connecting to, among others, PLCs.
Purdue Layer/Zone 3
Zone 3 encompasses functions for control and historical data, primarily including:
- Engineering Workstation (EWS): a dedicated computer for connecting to devices in Layers 0, 1, and 2.
- Historian: aggregates historical data for operational processes, used for analyzing past events.
Purdue Layer/Zone 3.5
Zone 3.5 incorporates the modernization required due to cybersecurity threats against OT environments, acting as a demilitarized zone (DMZ). This zone is a protective barrier between traditional IT environments and OT environments, ensuring direct connections between these two distinct environments do not occur. More traditional IT control systems, such as patch management, remote control, and similar functions, are placed in this zone.
Purdue Layer/Zone 4
Zone 4 represents the traditional IT environment, simplified into a single zone in this model, although it is often divided into multiple zones to ensure IT security. This zone typically includes:
- Workstations
- File servers
- ERP systems
- Printers
In a modern IT environment, it also encompasses cloud-based/SaaS services such as email, ERP, and other enterprise applications.
Cegal and the Purdue-model
Cegal's consultants are poised to support you in the realm of OT and cybersecurity. With our expertise in converged IT/OT environments and the security requirements therein, we can assist in both governance and technical aspects related to cybersecurity.
- SaaS
- Cyber security
- Operational Technology
- ERP
- EWS
- SCADA
- PLC/RTU
- NIS2